Most nonprofits don’t struggle because they ignore cybersecurity.
They struggle because every dollar has a job already assigned—programs, staff, services, fundraising—and technology rarely feels urgent until it interrupts the mission.
The problem is that attackers understand this reality very well.
From a managed IT partner’s perspective, nonprofits aren’t targeted because they’re careless. They’re targeted because they’re resource-constrained, data-rich, and built on trust. And that combination creates risk that leadership often isn’t given a clear way to evaluate.
This article breaks down what affordable cybersecurity for nonprofits really mean—and how to focus on what actually reduces risk, without overbuying or overcomplicating.
Table of Contents
Why Nonprofits Attract Attention (Even When They’re Small)
Nonprofits tend to hold more sensitive information than they realize:
- Donor and payment data
- Personal details about clients or beneficiaries
- Internal financial and grant information
- Access to partner systems and community networks
At the same time, most operate with:
- Small or part-time IT support
- Limited internal security expertise
- Older systems held together by good intentions
That gap—not size—is what attackers exploit.
Government agencies like CISA have been clear about this: nonprofits don’t need enterprise security programs, but they do need basic protections applied consistently.
The first step isn’t buying tools.
It’s deciding what level of risk leadership is willing to accept—and what’s simply too disruptive to ignore.
What “Affordable Cybersecurity” Actually Means for Nonprofits
Affordable cybersecurity is often misunderstood as “the cheapest tools available.”
In reality, it means:
- Spending time before money
- Prioritizing actions that reduce the most risk
- Avoiding complexity that staff can’t realistically maintain
For nonprofits, the most effective security strategies tend to share three traits:
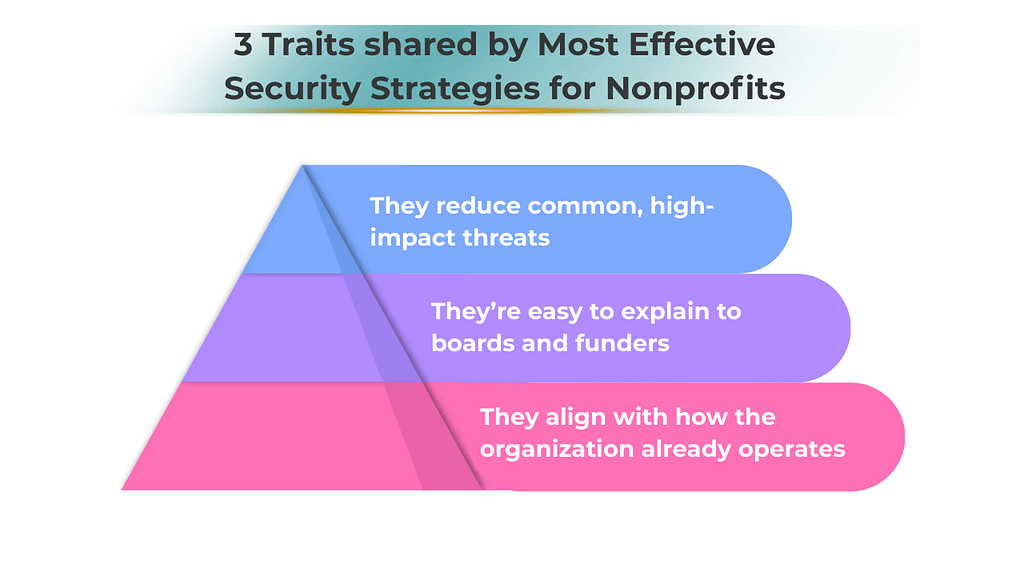
That’s why many MSPs anchor nonprofit guidance to recognized frameworks—not because leaders need to read them, but because they provide a defensible structure behind the scenes.
A Simple Way to Think About Security
Instead of starting with tools, it helps to ask four practical questions:
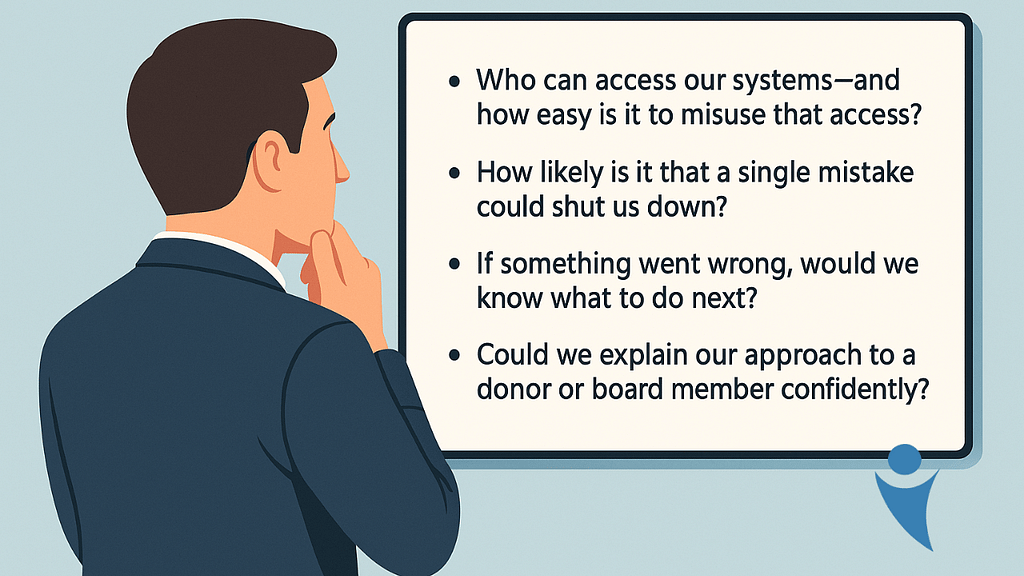
Good security programs—especially on tight budgets—are designed to answer those questions clearly.
The Highest-Value Actions Nonprofits Can Take First
When budgets are limited, some steps consistently deliver more protection than others.
1. Strengthen sign-ins (with minimal disruption)
Adding a second step to logins dramatically reduces account takeovers—often without adding licensing costs. For leadership, the real benefit isn’t technical; it’s operational stability.
2. Make email impersonation harder
Many nonprofit breaches start with convincing emails that look legitimate. Simple configuration changes can reduce how often staff are exposed to those messages in the first place.
3. Ensure data can be recovered, not just stored
Backups are often assumed to exist—until they’re needed. What matters most is not where data is stored, but whether it can be restored quickly.
4. Keep devices from becoming single points of failure
Lost or compromised laptops shouldn’t put the organization at risk. Basic device safeguards protect data even when hardware walks out the door.
How Much Is “Enough” at Different Budget Levels?
Rather than chasing perfection, nonprofits benefit from defining what reasonable looks like.
Very Small Budgets
The goal is basic protection and clarity:
- Strong sign-in practices
- Safer email handling
- Reliable backups
- Free or nonprofit-priced platforms
This alone eliminates many common attacks.
Modest Budgets
The focus shifts to visibility and consistency:
- Better protection on staff devices
- Simple training to reduce risky mistakes
- Clear expectations around access and data
At this stage, leaders can confidently say security is being managed—not ignored.
Larger or Growing Organizations
Here, the conversation becomes about resilience:
- Faster detection of issues
- Clear response plans
- Stronger protection for sensitive data
The goal isn’t fear—it’s continuity.
How We Frame This Conversation as an MSP
When advising nonprofits, we don’t lead with tools or threats. We focus on decisions leadership already cares about:
- Continuity: What would disrupt programs the most?
- Trust: What would damage donor confidence?
- Accountability: Could leadership explain their approach if asked?
Affordable cybersecurity for nonprofits works best when they support those outcomes—not when they compete with them.